Thursday, 11 April 2019
Wednesday, 23 December 2015
HOW TO KNOW WHO VISITS YOUR FACEBOOK PAGE/ VIEW YOUR PROFILE MOST
Want to know who has been admiring your pictures or follows you on Facebook secretly by viewing your profile often? Then read on.
We all have so many friends on Facebook, but how do we know those care or in one way or the other are more concerned about us by way of visiting our profile often due to admiration or secretly spying on our Facebook profile for reasons best known to them.
Below I share with you the trick to know who visits your Facebook profile most which can be best achieved on PC by following some simple steps.
1. Log-in to Facebook.
2. Go to your Facebook timeline and Right Click on your Timeline and select "View Page Source"
You'll be redirected to a new tab and page with lots of codes.
3. Click anywhere in the page and press and hold CTRL+F on your keyboard.
4. A text box appears at the top right corner. In that box type : (InitialChatFriendsList) without the brackets or better still copy and paste it in the text box without the brackets. Next to that word you'll see a list of Facebook ID numbers (100010676500301) which represents people who often visit your Timeline.
5. Go to Facebook.com, copy and paste the ID in the address bar after the (.com)
Example if the ID is 100010676500301 it should go like this: Facebook.com/100010676500301
The first ID visits your Timeline most followed by the second ID and it goes in that order.
Like and share if it works for you. Best regards.
We all have so many friends on Facebook, but how do we know those care or in one way or the other are more concerned about us by way of visiting our profile often due to admiration or secretly spying on our Facebook profile for reasons best known to them.
Below I share with you the trick to know who visits your Facebook profile most which can be best achieved on PC by following some simple steps.
1. Log-in to Facebook.
2. Go to your Facebook timeline and Right Click on your Timeline and select "View Page Source"
You'll be redirected to a new tab and page with lots of codes.
3. Click anywhere in the page and press and hold CTRL+F on your keyboard.
4. A text box appears at the top right corner. In that box type : (InitialChatFriendsList) without the brackets or better still copy and paste it in the text box without the brackets. Next to that word you'll see a list of Facebook ID numbers (100010676500301) which represents people who often visit your Timeline.
5. Go to Facebook.com, copy and paste the ID in the address bar after the (.com)
Example if the ID is 100010676500301 it should go like this: Facebook.com/100010676500301
The first ID visits your Timeline most followed by the second ID and it goes in that order.
Like and share if it works for you. Best regards.
Monday, 30 November 2015
ANDRIOD VIRUSES: HOW YOUR DEVICE CAN BE INFECTED & PROTECTION AGAINST THEM
 Android Viruses isn't a topic which many people discuss in my locality but there has really been complaints which some people I had met were not even able to describe. Picking up their devices I discovered they had been attacked by one form of virus or the other, that’s why I had to bring in this topic.
Android Viruses isn't a topic which many people discuss in my locality but there has really been complaints which some people I had met were not even able to describe. Picking up their devices I discovered they had been attacked by one form of virus or the other, that’s why I had to bring in this topic.A Brief Description of Android Viruses
Just like every other virus that can attack your computer systems, Android viruses are malicious apps, programs, files or even codes that can mess up your device and perhaps in most cases do things in your device without your consent, like stealing your data and/or destroying it.
They surely can do more harm to more devices despite the huge amount of effort Google puts into building Android OS. Many of us believe our Android devices are invulnerable but the OS is Open source (Android Open Source Project -AOSP), this alone completely changes that fact.
Android Virus Types
They are mainly Malwares and Trojans right now, they’re made up of files & codes, yes you heard me right “CODES”! Viruses are now written in strong encrypted codes and injected to run in your device, we take a sneak peak at Trojans & Malwares.
Malwares
Malwares can completely hijack installed apps with your data or even the entire device. This virus that use the WebView component on Android versions older than 4.4 (KitKat) are silent and transparent, it won’t notify you before taking actions.
Malwares make use of certificates to gain access to your device, Android certs which give administrative rights are basically of 3 types
1. Hard-coded Adobe certificate
2. The 3LM certificate with the certificate chain, malwares can use the device management extensions to silently install new apps, change system settings and take control of the device.
3. The third is hard-coded certificate is used by Google Wallet
Attackers abuse and can use any of the above certs to bypass whatever stops malwares from attacking your device.
Android Trojans
Okay, this one is pretty smart than the rest. If a trojan infects your device, it can relax there without you even noticing, it’s the most sophisticated virus you can think of.
Here’s a paragraph from Wikipedia of what Trojan can do.
“In August 2010, Kaspersky Lab reported a trojan designated Trojan-SMS.AndroidOS.FakePlayer.a.
This was the first malicious program classified as a Trojan SMS that affects smartphones running on Google’s Android operating system, and which had already infected a number of mobile devices, sending SMS messages to premium rate numbers without the owner’s knowledge or consent, and accumulating huge bills”
See what installing it looks like below…
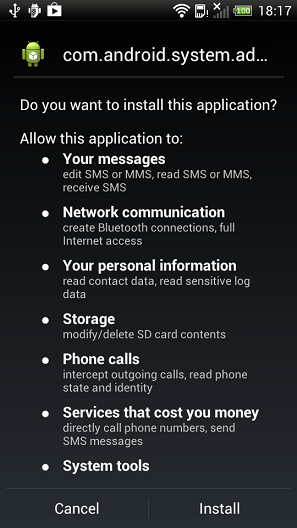
Another dreadful feature of a Trojan is that it can’t be deleted once it’s installed. This is because Trojan enjoys extended privileges, but is not listed as an application with Device Administrator privileges.
Trojans can go as Far as collecting sensitive data from your device and these may include: your MAC address, telephone number, account balance, local time and of course it will tell the cybercriminals whether it had successfully gained Administrator privileges of your device.
Now there were still apps submitted to Google and Kaspersky team for Analysis, they returned feedbacks after scanning– trojans make use of a program called “Backdoor.AndroidOS.Obad.a.”
I believe more crafty ways are still been built to encrypt Trojans with codes that cannot be understandable by anti-malware experts. The fight against this virus continues.
How Your Android Devices can Be Infected
Your device can be infected through any means of communication with a 3rd-party device, app, files, or bytes it received.
In most cases those free apps you install from 3rd party stores other than the original Google PlayStore can contain malicious codes.
You may even get your device infected through mails/messages attachments, or shared apps from another devices.
Tips on how to protect your device
Fortunately, in most cases of reported issues of Android malware & trojan attacks, solutions were quickly created to fight it. Here’s what you can do in case your smartphone or tablet is already infected:
1. Install an ANTI-VIRUS
Installing an antivirus can’t be overemphasized. Although this does not guarantee your device is 100 secure, it goes a long way to prevent an infection. You may pick from any of those below, they’re reliable.
– Kaspersky Internet Security
– AVAST Mobile Security & Antivirus
There are more which you can always find from recommendation by Play Store.
You’re expected to install only one AntiVirus! Installing more than one can actually harm your device sooner or later. Wondering why? Installing two different programs to perform the same jab can cause conflicts with undesirable effects like your device crashing or slowing down.
I’ll suggest you also install Bluebox Security Scanner, it can check whether a device is vulnerable to the fake ID attacks and whether your device allows installation of apps from untrusted sources among other things.
2. Monitor Your Installation Permissions & Accessibility
Before installing apps, you’re always presented with the permissions the app is asking for. This is an easy way to spot malicious programs. When apps starts asking for permissions like your contacts, device app history, location, identity, SMS access, email access and other sensitive data, be sure it’s an app you trust downloaded preferably from Google Play.This includes
You can also choose to VERIFY APPS before you install them.
3. Encrypt your phone
With this settings activated, you should make yourself a numeric PIN or Password to decrypt your phone each time you Power it on. You do this by going to SETTINGS > SECURITY > scroll down and you’ll find the option.
Be sure you use a PIN/Password you can easily remember.
People feel Android virus attacks are few but it mustn't be ignored, otherwise you may loose not only your device, but also your accounts connected with it. Apps like PayPal, GoogleWallet, BitCoin can get hacked through viruses. I still can’t tell which viruses are more harmful, but I’m pretty sure the tips in this post will help you stay safe from any of them.
All the best.
Wednesday, 24 June 2015
HOW TO MUTE/SILENCE WHATSAPP GROUP NOTIFICATION SOUNDS/TONES

I therefore decided to give the below tutorial which may be known or unknown to many.
1. On your Whatsapp Chat/conversation menu, go to Settings, then Notifications.
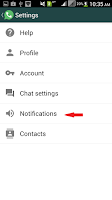
2. Select Notifications and scroll down to Group Notifications.
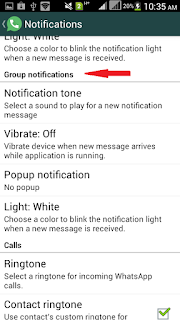
3. Tab on Notification Tones and Select Silent or None and ok it.
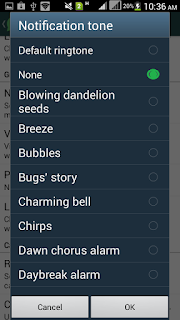
You are done.
Wednesday, 17 June 2015
WINDOWS XP SUPPORT ENDED LAST YEAR, 2014
 Microsoft first released Windows XP on October 25, 2001 and after over twelve years of supporting the operating system announced it is ending Windows XP support April 8, 2014 which means that they will no longer be providing any updates, patches, or further software security related support.
Microsoft first released Windows XP on October 25, 2001 and after over twelve years of supporting the operating system announced it is ending Windows XP support April 8, 2014 which means that they will no longer be providing any updates, patches, or further software security related support.
If you are still running Windows XP it will continue to work after this date, but if a security vulnerability is discovered after this date it will not be fixed by Microsoft. However, Microsoft has indicated it will continue to offer anti-malware support (MSE) for Windows XP until July 14, 2015 and other anti-virus manufacturers have also announced that they'll be extending their support of Windows XP for up to a year. While this will offer some protection for your computer it still will not protect against any new vulnerabilities not yet released or discovered.
Some people argue that since Windows XP is such an established operating system that it is not likely that any new security vulnerabilities will be discovered. However, most experts recommend upgrading to a later version of Windows, either Windows 7 or the latest version of Windows, Windows 8.
If your computer is over four years old or does not meet the system requirements of a new versions of Windows we suggest getting a new computer with a more up-to-date version of Windows. Alternatively if you want to keep the older computer and don't need Windows you may also consider switching to Linux distro.
Tip: Microsoft is offering a free data transfer program for users upgrading from Windows XP to Windows 7, 8, or 8.1.
Tip: If your hesitation of going to a new version of Windows is because you have an older program that is designed for Windows XP, Windows XP Mode can help older programs run in new versions of Windows.
What if I still want to run and use Windows XP?
If you plan on continuing to use Microsoft Windows XP after April 8, 2014 following the below suggestions.
- Don't use an administrator account - Use a limited account and not a adminaccount. If you use an account with not enough rights spyware, malware, and other exploits wont work or be much less likely to work.
- Use an alternative browser - Don't use Internet Explorer and instead use an alternative browser such as Chrome or Firefox, which will continue to be updated and remain secure.
- Keep your browser plugins and extensions updated - Plug-ins like Java and Flash are one of the most common methods of attacking a computer. Keep your browser and all of its plug-ins up-to-date. You can find the latest version of all your plug-ins through our system information tool. If you don't use a plug-in that is installed (e.g. Java, uninstall it from the computer.)
- Keep the computer offline - If this is a work computer that doesn't need to be online keep it offline. Without having access to the Internet the computer cannot be attacked.
- Follow all the steps on how to protect yourself while online.
Related questions
Can Windows XP still be installed and activated after April 8, 2014?
Yes. You'll still be able to run, install, and activate Windows XP after April 8, 2014.
What about Windows XP Embedded?
Windows XP Embedded support will remain until January 12, 2016.
Saturday, 8 November 2014
MICROSOFT KEY BOARD SHOTCUTS
Ctrl + 0
|
Adds or
removes 6pts of spacing before a paragraph.
|
Ctrl + A
|
Select all
contents of the page.
|
Ctrl + B
|
Bold highlighted selection.
|
Ctrl + C
|
Copy selected text.
|
Ctrl + D
|
Open the font preferences window.
|
Ctrl + E
|
Aligns the
line or selected text to the center of the screen.
|
Ctrl + F
|
Open find
box.
|
Ctrl + I
|
Italic highlighted selection.
|
Ctrl + J
|
Aligns the
selected text or line to justify the screen.
|
Ctrl + K
|
Insert link.
|
Ctrl + L
|
Aligns the
line or selected text to the left of the screen.
|
Ctrl + M
|
Indent the
paragraph.
|
Ctrl + P
|
Open the
print window.
|
Ctrl + R
|
Aligns the
line or selected text to the right of the screen.
|
Ctrl + T
|
Create a
hanging indent.
|
Ctrl + U
|
Underline
highlighted selection.
|
Ctrl + V
|
Paste.
|
Ctrl + X
|
Cut selected text.
|
Ctrl + Y
|
Redo the last
action performed.
|
Ctrl + Z
|
Undo last
action.
|
Ctrl + Shift
+ L
|
Quickly
create a bullet point.
|
Ctrl + Shift
+ F
|
Change the
font.
|
Ctrl + Shift
+ >
|
Increase
selected font +1pts up to 12pt and then increases font +2pts.
|
Ctrl + ]
|
Increase
selected font +1pts.
|
Ctrl + Shift
+ <
|
Decrease
selected font -1pts if 12pt or lower, if above 12 decreases font by +2pt.
|
Ctrl + [
|
Decrease
selected font -1pts.
|
Ctrl + / + c
|
Insert a cent
sign (¢).
|
Ctrl + ' +
|
Insert a
character with an accent (grave) mark, where
|
Ctrl + Shift
+ *
|
View or hide non printing
characters.
|
Ctrl +
|
Moves one
word to the left.
|
Ctrl +
|
Moves one
word to the right.
|
Ctrl +
|
Moves to the
beginning of the line or paragraph.
|
Ctrl +
|
Moves to the
end of the paragraph.
|
Ctrl + Del
|
Deletes word
to right of cursor.
|
Ctrl +
Backspace
|
Deletes word
to left of cursor.
|
Ctrl + End
|
Moves the
cursor to the end of the document.
|
Ctrl + Home
|
Moves the
cursor to the beginning of the document.
|
Ctrl +
Spacebar
|
Reset
highlighted text to the default font.
|
Ctrl + 1
|
Single-space
lines.
|
Ctrl + 2
|
Double-space
lines.
|
Ctrl + 5
|
1.5-line
spacing.
|
Ctrl + Alt +
1
|
Changes text
to heading 1.
|
Ctrl + Alt +
2
|
Changes text
to heading 2.
|
Ctrl + Alt +
3
|
Changes text
to heading 3.
|
Alt + Ctrl +
F2
|
Open new
document.
|
Ctrl + F1
|
Open the Task Pane.
|
Ctrl + F2
|
Display the print preview.
|
Ctrl + Shift
+ >
|
Increases the
highlighted text size by one.
|
Ctrl + Shift
+ <
|
Decreases the
highlighted text size by one.
|
Ctrl + Shift
+ F6
|
Opens to
another open Microsoft Word document.
|
Ctrl + Shift
+ F12
|
Prints the
document.
|
F1
|
Open Help.
|
F4
|
Repeat the
last action performed (Word 2000+)
|
F5
|
Open the
find, replace, and go to window in Microsoft Word.
|
F7
|
Spellcheck
and grammar check selected text or document.
|
F12
|
Save as.
|
Shift + F3
|
Change the
text in Microsoft Word from uppercase to lowercase or a capital letter at the beginning
of every word.
|
Shift + F7
|
Runs a
Thesaurus check on the word highlighted.
|
Shift + F12
|
Save.
|
Shift + Enter
|
Create a soft break instead of a new paragraph.
|
Shift +
Insert
|
Paste.
|
Shift + Alt +
D
|
Insert the
current date.
|
Shift + Alt +
T
|
Insert the
current time.
|
In addition to
the above shortcut keys users can also use their mouse as a method of quickly
do something commonly performed. Below some are examples of mouse shortcuts.
Mouse shortcuts
|
Description
|
Click, hold,
and drag
|
Selects text
from where you click and hold to the point you drag and let go.
|
Double-click
|
If
double-click a word, selects the complete word.
|
Double-click
|
Double-clicking
on the left, center, or right of a blank line will make the alignment of the
text left, center, or right aligned.
|
Double-click
|
Double-clicking
anywhere after text on a line will set a tab stop.
|
Triple-click
|
Selects the
line or paragraph of the text the mouse triple-clicked.
|
Ctrl + Mouse
wheel
|
Zooms in and
out of document.
|





